
DJango : Private Content Streaming using Amazon S3
In one of our recent project we had a requirement of streaming a video, to only a specific set of users who have subscribed to our content.
We were using AWS S3 bucket to store our media files. By default if you upload a file on S3, it’s private and not accessible to anyone except the account owner. So that achieved fifty percent of our task, but now we had to focus on sharing the files to a specific set of users who have subscribed to our service.
AWS provides a unique feature of generating a signed URL. We can add a time limit until which that URL is valid.
Below is the code to generate a signed URL
So now we have a URL which was only accessible for 15 mins
generate_url parameters
expires_in represents the time in seconds after which the URL is invalid
query_auth if set to true it will sign the request in the URL
force_http if set to true it will create http URL instead of https
But when we used the URL in VLC or other media player, the video was played until the URL expired. Which undermined the whole motive of restricting the access.
AWS Bucket Policy to the rescue
To allow read access to our private objects i.e our videos only from our website, we need to add a bucket policy that allows s3:GetObject permission with a condition, using aws:referer key, that the get request must originate from specific webpages.
So we added the following snippet into our AWS bucket policy,
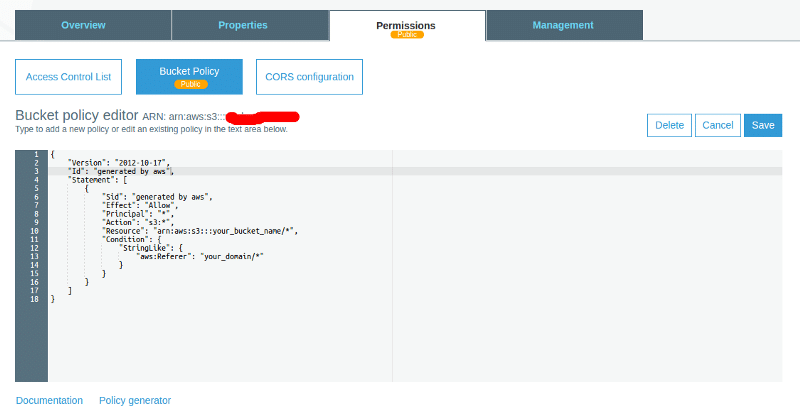
Policy generator option under the Bucket Policy tab will help generating the policy, after which you can make the necessary changes to it. Please refer
AWS Policy Generator
AWS Policy Generatorawspolicygen.s3.amazonaws.com
- For the first step to select the policy type choose S3 Bucket Policy
- Then for Principal field use * and for Actions choose GetObject
- Click on Add Condition, it will show you the following
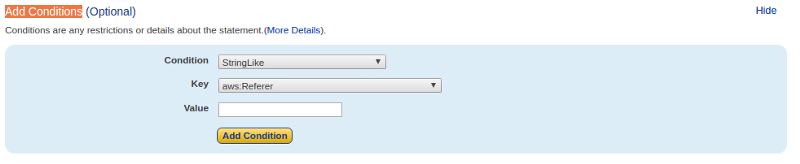
- For the Condition select the StringLike option
- Key should have aws::Referer and Value should be your domain name eg http://www.example.com/*
- Once the policy is generated you can paste it into the Bucket Policy page as per the content mentioned previously.
After saving now all the private contents are accessible from our domain only.
But now we need to remove the code for generating a signed URL, as that piece of code overrides the bucket policy.
Once that is removed all media content, though it is private, will be accessible only through our domain.
Click here for more details…
At BoTree Technologies, we build enterprise applications with our Django team of 20+ engineers.
We also specialize in RPA, AI, Python, Ruby on Rails, JavaScript and ReactJS.




